There are 5 Levels of Carding.Carding is a type of cybercrime where stolen credit or charge card data is utilized to make unauthorized buys. Whereas illicit, carding has distinctive levels of complexity that extend from fundamental to profoundly modern operations.
1. Basic Levels of Carding:
At the basic level, individuals often have little technical knowledge. We rely on pre-made tools and simple methods to carry out carding activities.This level is direct and is an suitable beginning point for people who are destitute and looking to learn carding essentials Levels of Carding. This category caters to those who wish to arrange dinners, little orders for nourishment over the phone from eateries, or through administrations such as Uber Eats, and so forward. If you expected to be a Level 1 carder, you may continue to ask a feast or a few dinners utilizing the credit card data you have secured. In quintessence, it is as uncomplicated as utilizing a friend’s credit card found in their wallet to put an arrange Levels of Carding.
Requirements:
- Expiry Date of Card
- CC(CreditCard) number
Common Activities:
- Buying stolen card data from dark web forums
- Using public card-checking websites to verify if the card is active
- Simple phishing attacks to steal card details
Tools Used:
- Free VPNs for hiding identity
- Basic card checkers
- Phishing kits available online
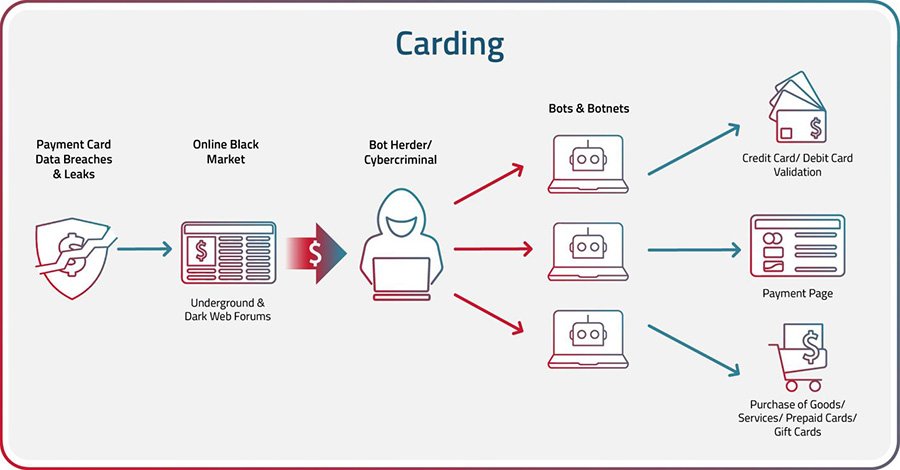
2. Intermediate Levels of Carding:
Intermediate carders have more knowledge of cybersecurity and fraud detection systems. We use advanced methods to bypass security measures.This is the level at which most people enter when commencing with carding, which is an great beginning point for newcomers to credit card extortion. If you proposed on being a level 2 carder, you are focusing on things that are overwhelmingly beneath $500 USD and accost from littler online businesses Levels of Carding. These websites ought to be one of a kind and lesser known when chosen for carding, whereas maintaining a strategic distance from VBV. I suggest centering on littler, neighborhood businesses with online retail outlets. Point to card low-level targets (clothing stores, etc.), so start considering what you consider a low-level target Levels of Carding.
Requirements:
- CC(CreditCard) number
- Expiry Date of Card
- CVV (Card Verification Value)
- Date of Birth
- Billing Adress
- Name of Cardholder
- Mobile Number
- RDP/Socks
Common Activities:
- Setting up fake e-commerce websites for phishing scams
- Exploiting weak payment systems to process stolen card data
- Using social engineering techniques to trick people into revealing sensitive information
Tools Used:
- Advanced VPNs and proxy servers
- Remote Desktop Protocols (RDPs) for anonymity
- Automated carding bots
Carders at this level aim for larger transactions and more profitable scams Levels of Carding.

3. Advanced Levels of Carding:
At this stage, carding becomes part of organized cybercrime. Groups work together to commit large-scale fraud, often targeting businesses and financial institutions.Level 3 carders are prepared people who have a profound understanding of carding online and have formulated a strategy they accept to be dependable when requesting things online. This would envelop orders from any major retailer for higher esteem things such as hardware, tablets, little apparatuses, and so forward, and have obtained the data to avoid VBV. I came to get it when I was an “level 3 carder” that acquiring things online includes a noteworthy sum of trial and blunder went with with disappointment at each turn. Numerous hours went through getting the legitimate cards, putting online orders, orders being cancelled, drops being compromised, requiring distinguishing proof to claim the thing, and so on Levels of Carding.
Most of us all accept that once we dive into carding, we’re going to make a fortune but you before long figure it out that offering things online utilizing a stolen credit card, getting them transported effectively to a drop, and at that point re-selling that protest isn’t going to be a way of hoarding that riches. There are various components that are troublesome to co-ordinate and control to work in your support in this sort of duplicity Levels of Carding.
Requirements:
- Credit Card Number (CC)
- Expiry Date on the card
- CVV (Card Verification Value)
- Name of Cardholder
- Date of Birth
- Charging Address
- Phone number (subordinate on situation)
- Credit report / Foundation check (in an endeavor to verify VBV questions)
- National Protections Number
- Drop address to recover your purloined goods
- On event, require a fake ID in arrange to collect things shipped
- Mail of the card holder or in a perfect world get to to the mail account of the card holder
- RDP or SOCKS IP that is as near to card holder address as conceivable.
Common Activities:
- Hacking into databases to take enormous sums of card data
- SIM swapping to bypass two-factor verification (2FA)
- Laundering stolen money through complex networks
Tools Used:
- Custom malware designed to steal payment information
- Encrypted communication platforms for secure coordination
- Botnets to robotize large-scale attacks
These operations are modern, with each part playing a particular part, such as programmer, information dealer, or cash launderer. Levels of Carding
4. Expert Levels of Carding:

At the expert level, carding activities are highly advanced and often linked to international crime syndicates.Level 4 carders are people who clone people’s credit cards, enter a store with daringness, make a buy in individual, and exit instantly. In this way, they either offer the thing online or keep it for themselves, as these merchandise are profoundly profitable. Level Four carders tend to be more prepared, more seasoned in age, learned approximately misdirection, and have life encounter. They have this statistic as they get it the prerequisites to gotten to be a effective Level Four carder, or any genuine fraudster.Levels of Carding
Level Four carders are likely to “act” and have amazing social aptitudes, acting as effective social engineers. If working at this level, treat the stolen credit card in your hand as bona fide. Continuously watch the person you will hand the card to. Lock in in a normal discussion, utilizing social designing to your advantage.
Being in a area with cameras, witnesses, and IoT gadgets increments hazard altogether. This is outstandingly diverse from committing cybercrimes versus committing real-life crimes Levels of Carding.
Consider individual capabilities for any victory. Age, social abilities, physical appearance, demeanor, and development are imperative. If tall on cocaine (as right now), for case, do not mixed up yourself for showing up satisfactory. Levels of Carding
Requirements:
- Credit Card Number (CC)
- Card Close Date
- Card Confirmation Esteem (CVV)
- Track 1 and 2 Information (CVV DUMPS)
- Credit card perusing and composing hardware (MSR605x, MSR605, AMC722)
- Clear Cards / PVC Cards
- Credit Card / I.D Printer
- Embossing Machine
Common Activities:
- Developing zero-day exploits to target secure financial systems
- Running global money laundering schemes using cryptocurrencies
- Selling Fraud-as-a-Service (FaaS) tools to other criminals
Tools Used:
- Advanced Persistent Threats (APTs) for long-term attacks
- Custom-built hacking tools and software
- Private encrypted networks for communication
5. Mastermind Levels of Carding:

The Mastermind level represents the pinnacle of carding operations. Individuals or groups at this level not only engage in carding but also design, develop, and control large-scale cybercrime ecosystems.These sorts of carders contact businesses and put an arrange for a item over the phone. They give the CC points of interest over the phone to the dealer and at that point collect the item at a afterward time. These people ordinarily have a comprehensive information of development work, extend administration coordinations, building supplies, and other gear required for large-scale development items. It is very common for level 5 carders to use a stolen corporate CC to put a store on a piece of rental hardware and slip away with it.
Level 5 carders work additionally to a level 4 carder; in any case, there is a slight variety in their coordinations and tactics.
CONCLUSION
Now that one is familiar with the changing degrees of carders, it ought to be clear which level one falls into and what is practically achievable for oneself. As can be watched, each level requires unmistakable commodities and expertise sets in arrange to prosper. Not as it were does this require varying things, but it too requests expanded self-assurance, a characteristic that regularly controls numerous people from trying in this frame of deception.
This is a acknowledgment characteristic to carding. Notwithstanding of the way chosen, at slightest presently one has the essential data to make an educated choice concerning the fittingness of this sort of extortion for oneself.Levels of Carding
Requirements:
- Credit Card Number (CC), ideally business
- CVV code
- Clear cards / PVC cards with implanted chips
- Expiry Date on the card
- Embossing machine
Common Activities:
- Orchestrating international carding networks and syndicates
- Creating and distributing proprietary fraud tools, malware, and exploits
- Coordinating multi-layered attacks targeting governments, financial institutions, and critical infrastructure
Tools Used:
- Artificial Intelligence (AI) and Machine Learning (ML) for automated fraud detection evasion
- Quantum encryption techniques for unbreakable communication security
- Custom-designed hardware for secure data processing and anonymization
More Hacking Courses are coming soon in Urdu/Hindi Languages Soon as possible for now you can check out our website carding Methods Blackhat Pakistan and our YouTube channel Blackhat Pakistan. carding And Spamming full course in Urdu/Hindi
Also Checkout our website Grayhatempire.com for more tools. if you want to Download CraxsRat 7.4 Cracked then check here. For Requesting New Program Request us on Grayhatempire Telegram.
Also Don,t forget to Visit Blackhat Pakistan. Also Checkout Hap Crypter Cracked.

